Privacy-enhancing
technology
Business growth and risk mitigation for the new data economy

Overview
2019-2021
Lead/sole product designer at QEDIT working with the VP Product and development team to create platform/s for various uses cases.


Problem
How to make this technology usable
Our challenge was to transform a technical solution, initially API-based with no physical product interaction, into a user-friendly platform. To effectively sell this solution and provide tangible value, we needed to develop a user interface for interacting with the technical solution, expanding its utility.
The technical solution leverages cryptographic techniques to safeguard Personally Identifiable Information (PII) while enabling comparisons and insights into sensitive business data. Initially, we could provide dataset comparisons via command-line interface (CLI), but it was insufficient as a product. Our task was to design a comprehensive solution that streamlines dataset organization, facilitates collaboration and comparison across organizations, delivers and analyzes results, and automates processes based on these outcomes. Additionally, accommodating diverse use cases required designing multiple platforms to cater to individual needs.
Design process
Research
We possessed a technical solution but lacked a clear understanding of our potential customer base, as our target audiences varied across different use cases for the technology. My initial research focused on identifying the ideal customer profiles for each use case:
-
HR professionals for certification management
-
Chief Marketing Officers for marketing and business growth
-
Risk and compliance teams within insurance and financial services
Given the novelty of privacy-enhancing technology and limited existing products, many organizations are aware of privacy regulations but may not yet be aware of available solutions. To gauge awareness levels and guide customer interviews effectively, we use this awareness barometer as a reference for asking pertinent questions.
Scale of awareness
Our potential users are here
Aware of problem but
not aware of a solution
Problem/Solution aware & using a competing product
Unaware of problem
Problem & solution aware but don't know or use a product for this solution
How to use personas
Rather than creating static personas, I sought commonalities among these use cases and feedback from individuals associated with them to define the foundational product.
We conducted interviews with our ideal and potential customers across all use cases. Initially, I developed prototypes for each individual use case, revealing substantial overlap in their objectives. This common ground allowed us to construct a single core platform capable of supporting multiple use cases.
Subsequently, we used the prototypes to assess the specific goals and variations among personas. If a more tailored solution was required, our understanding evolved through interactions with the prototypes and, later, the MVP, which centered around a more unified and versatile product.






Initial sketches that led to individual prototypes that we built in order to understand the various use cases. Click to enlarge.
Video of the prototype I built to get internal buy-in on creating one platform for all the use cases
Proof of concept
Learnings
Following the prototype demoand conducting a proof of concept with two companies focused on business growth, a primary concern emerged: the results were not informative. The issue stemmed from the use of identifiers (row IDs) that were not directly linked to the raw data's IDs. Consequently, users had to download and reintegrate these results into platforms like Excel to grasp their value and work with them effectively.

Before
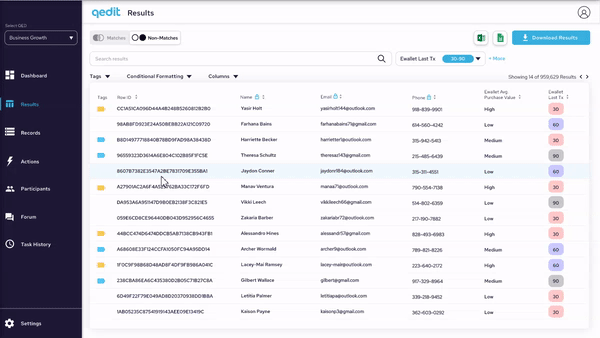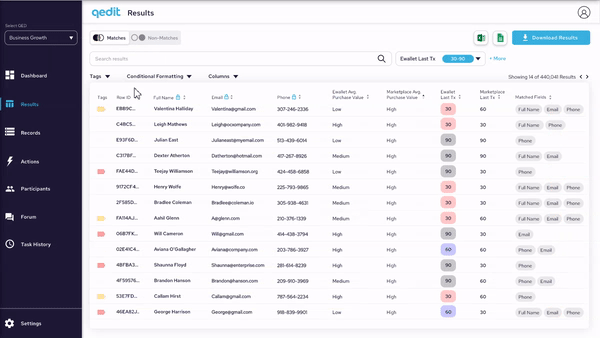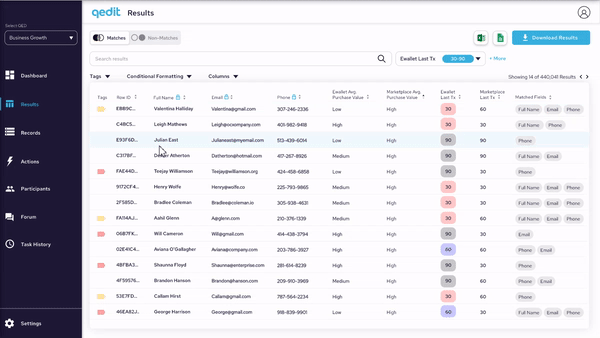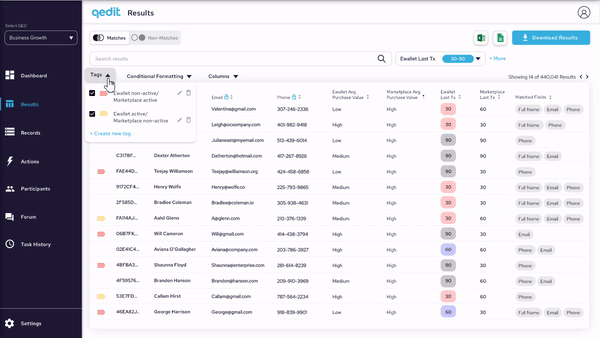
Results table is not usable in this state. The results must be downloaded then uploaded into an excel sheet in order to work with the data.
The identifier (row_id) is not understood. Although it proves that the data is in fact encrypted, the end-user cannot easily decipher which person is associated with the row_id.
The matched criteria is not understood in this design. What is matched criteria?

After
Results can be filtered, sorted, highlighted, tagged, and arranged in order to facilitate usability and ease of visibility.
By implementing privacy-enhancing technologies, we are able to show real data without compromising any personally identifying information or data leaks through the system.
The matched criteria is completely visible, allowing the users to understand the risk of each case fully.
Key problem solved: reduce time on task

Data Input:
Setting up data in order to collaborate takes a lot of time to makes sure all the datasets are formatted correctly. By allowing for integrations with common data sources and creating a platform that helps you easily check that the data inputs are formatted correctly, we can reduce the time on task.

Automations:
Allow for users to be able to select from multiple different actions based on varying result outcomes. Reducing time on task for the risk and compliance teams involved and allowing for integrations with platforms they already use internally to manage flagged or risky behavior. Dropdowns allow for them to select custom actions and New action button allows them to create new actions based on criteria of their choosing.
Outcome
The existing secure data collaboration platform is in its MVP phase, actively utilized by two companies in the business growth use case, and currently undergoing pilot testing with organizations in the insurance and financial services sector.
Leveraging tools like Hotjar and Google Analytics, we identified that users were dedicating significant time to the dashboards, which informed our strategy to enhance them further.
The Proof of Concept (POC) phase holds utmost importance as it provides vital insights for iterative improvements in subsequent versions, allowing us to refine and expand the product.
Dashboards
MVP integration
For the MVP we used a Quicksite integration for the dashboard in order to better determine what kind of graphs and charts would be more useful to users. Based on user feedback we know now that we can build more customized dashboard in future versions.





Sketches and dashboard designs for future customizations
Designing for
emerging technologies
A designer's role
As a designer in an innovative field working with emerging technologies, my role extends beyond crafting user-friendly interfaces; it involves building user trust. While users may not grasp the underlying technologies, they must have confidence in data security and goal attainment.
Establishing trust involves leveraging established UX/UI principles to create a sense of familiarity and utmost transparency. By elucidating background processes to users, we foster a deeper level of trust in the system.


